Everything about Cyber Security Company
Chicago Security Guards & Cyber Security Service";var b="+17734454300";var c="";var d="7545 S Western Ave, Chicago, IL 60620, United States";var e="";var f="";var arr=[];arr.push(decodeURIComponent("%3Cdiv%3E%3Cdiv%20style%3D%22padding%3A%208px%3B%20border%3A%202px%20solid%20grey%3B%22%3E%3Ch3%20style%3D%22margin-top%3A%204px%3Bmargin-bottom%3A0px%22%3E"));arr.push(a);arr.push(decodeURIComponent("%3C%2Fh3%3E"));arr.push(decodeURIComponent("%3Cbr%3EAddress%3A%20"));arr.push(d);arr.push(decodeURIComponent("%3Cbr%3EPhone%3A%20%3Ca%20href%3D%22tel%3A"));arr.push(b);arr.push(decodeURIComponent("%22%3E"));arr.push(b);arr.push(decodeURIComponent("%3C%2Fa%3E"));arr.push(decodeURIComponent("%3Cbr%3E%20%3C%2Fdiv%3E"));document.querySelector('#_nap_').innerHTML = arr.join('');The quantity of cyber attacks as well as data violations in recent years is incredible as well as it's very easy to generate a laundry checklist of business that are house names that have been influenced. The Equifax cybercrime identity burglary occasion influenced roughly 145.
In this instance, safety and security inquiries and also solutions were additionally endangered, raising the threat of identity burglary. The violation was first reported by Yahoo on December 14, 2016, as well as compelled all affected individuals to alter passwords and also to reenter any unencrypted safety inquiries and also solution to make them secured in the future.
The 9-Minute Rule for Cyber Security Company
Cybersecurity is similar to a bar or a club that weaves with each other several measures to shield itself as well as its clients. Baby bouncers are positioned at the entries. They have strategically put CCTV cameras to maintain an eye out for questionable actions. They have thorough insurance plan to protect them against every little thing from burglaries to legal actions.
See This Report about Cyber Security Company
Spyware is a malware program created with the single purpose of collecting details as well as sending it to one more device or program that is obtainable to the attacker. The most usual spyware typically videotapes all customer activity in the gadget where it is set up. This results in opponents figuring out sensitive information such as credit score card information.

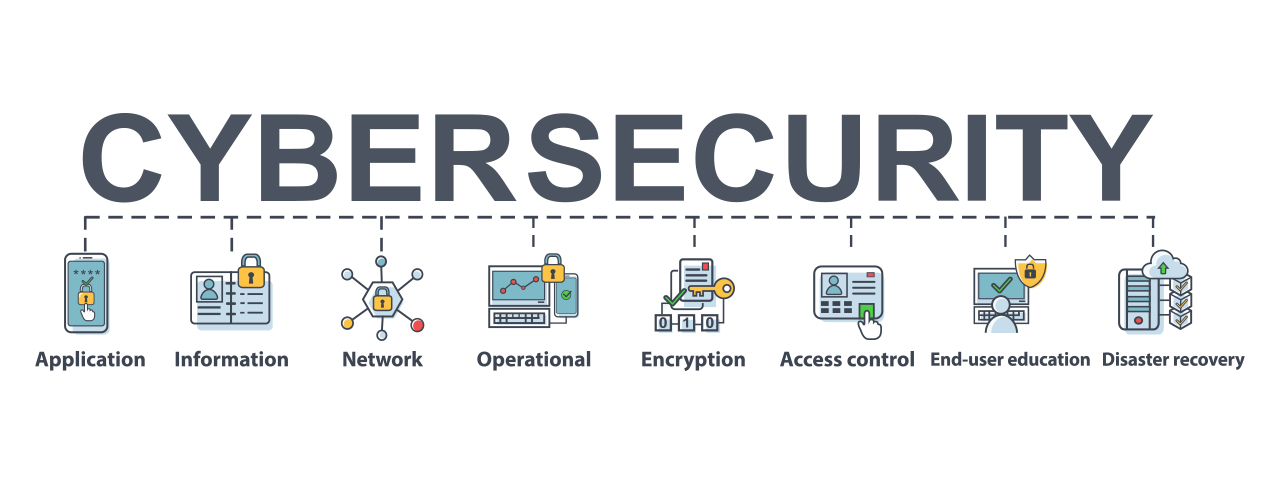
Cybersecurity is a huge umbrella that covers different protection components. It is simple to obtain overloaded and also shed concentrate on the huge photo. Here are the leading ten best techniques to comply with to make cybersecurity efforts much more reliable. A cybersecurity plan should start with determining all elements of the facilities as well as users that have accessibility to them.
Cyber Security Company Things To Know Before You Get This
This is either done by web solutions revealed by each remedy or by making it possible for logs to be readable among them. These remedies should have the ability to expand in tandem with the company and with each other. Misplacing the latest safety and security patches and updates is very easy with multiple protection options, applications, systems, as well as devices entailed - Cyber Security Company.
The even more critical the resource being safeguarded, the a lot more frequent the upgrade cycle requires to be. Update strategies should be part of the first cybersecurity plan.
Everything about Cyber Security Company
The National Cyber Safety Alliance recommends a top-down approach to cybersecurity, with company administration leading the fee throughout company processes. By incorporating input from stakeholders at every level, even more bases will be covered. Also with the most sophisticated cybersecurity technology in link position, the onus of safety and security usually drops on completion individual.
An enlightened worker base tends to boost safety pose at every level. It appears that despite the industry or dimension of a company, cybersecurity is a developing, necessary, and also non-negotiable procedure that i loved this grows with any kind of business. To make sure that cybersecurity efforts are heading in the appropriate instructions, the majority of countries have controling bodies (National Cyber Safety Centre for the U.K., NIST for the united state, etc), which release cybersecurity guidelines.
Cyber Security Company Things To Know Before You Buy
We performed a study to much better comprehend exactly how boards deal with cybersecurity. We asked directors how often cybersecurity was gone over by the board and located that just 68% of respondents claimed consistently or regularly.
When it involves comprehending the board's duty, there were several alternatives. While 50% of respondents stated there had been conversation of the board's role, there was no consensus concerning what that duty ought to be. Supplying assistance to operating supervisors or C-level leaders was seen as the board's function by 41% of respondents, taking part in a tabletop workout (TTX) was discussed by 14% of the respondents, and general recognition or "on call to respond needs to the board be needed" was discussed by 23% of Supervisors.
About Cyber Security Company
There are numerous structures readily available to assist an organization with their cybersecurity strategy. It is straightforward as well as offers executives as well as directors a great structure for believing via the essential elements of cybersecurity. It likewise has several levels of information that cyber specialists can make use of to set up controls, processes, and procedures.